Phishing Alert: Malicious Campaign Impersonates Astound/RCN Using Webflow and Wix
Date: September 25, 2025
Author: SaberGuard Threat Intelligence Team
SaberGuard has identified and blocked an active phishing campaign impersonating Astound/RCN. The attackers abused compromised business email infrastructure and well-known web platforms to deliver a phishing lure and a silent malware dropper.
We are sharing this advisory publicly to raise awareness, as no other public disclosures of this threat were available at the time of discovery.
How the Attack Worked
Phishing Email
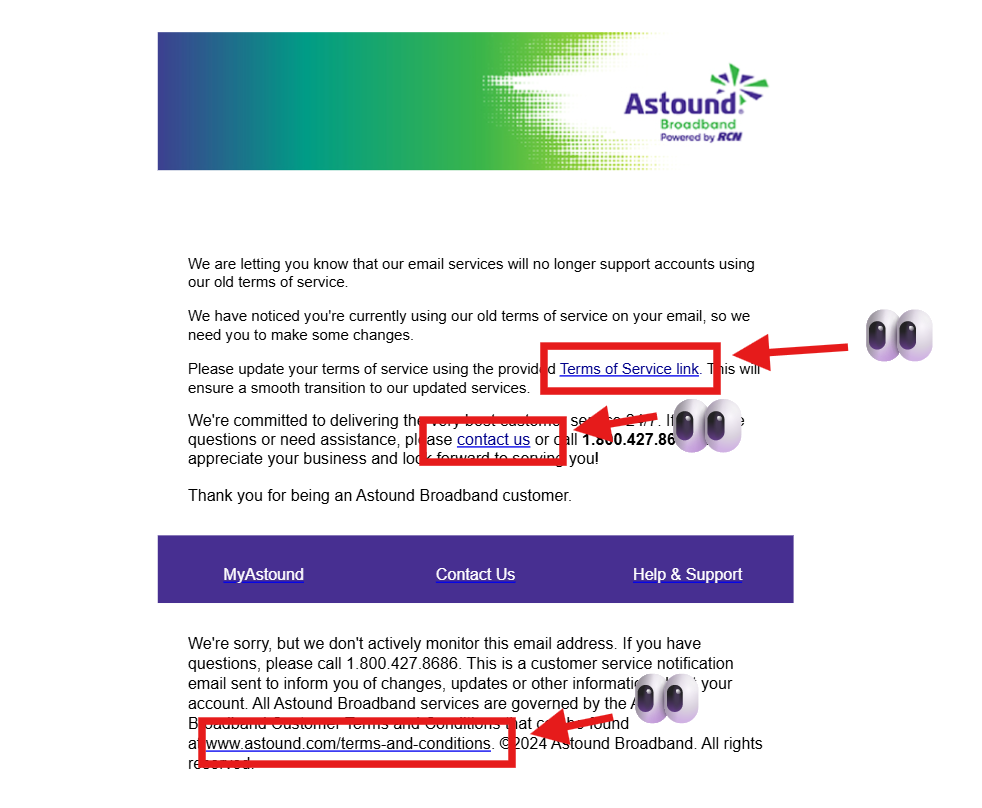
Victims received emails appearing to come from an RCN-branded sender.
Technical headers show the message originated from an authenticated third-party business account that appears to have been compromised.
(Exact sender account and infrastructure details have been redacted for this public advisory.)
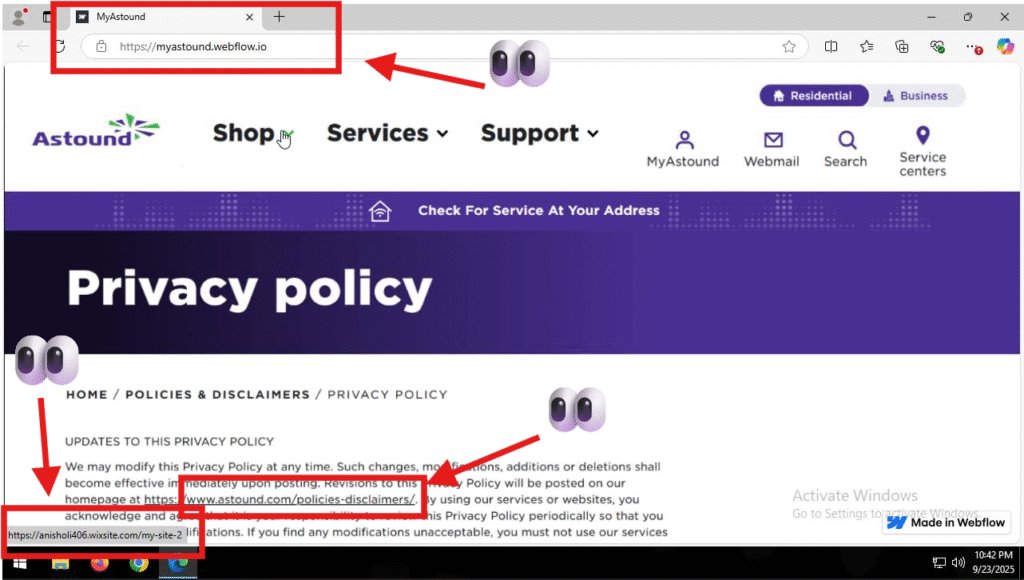
Fake Astound Login Page
Users were directed to a malicious Webflow-hosted page mimicking an Astound login/update prompt.
URL (defanged):
hxxps://myastound[.]webflow[.]io
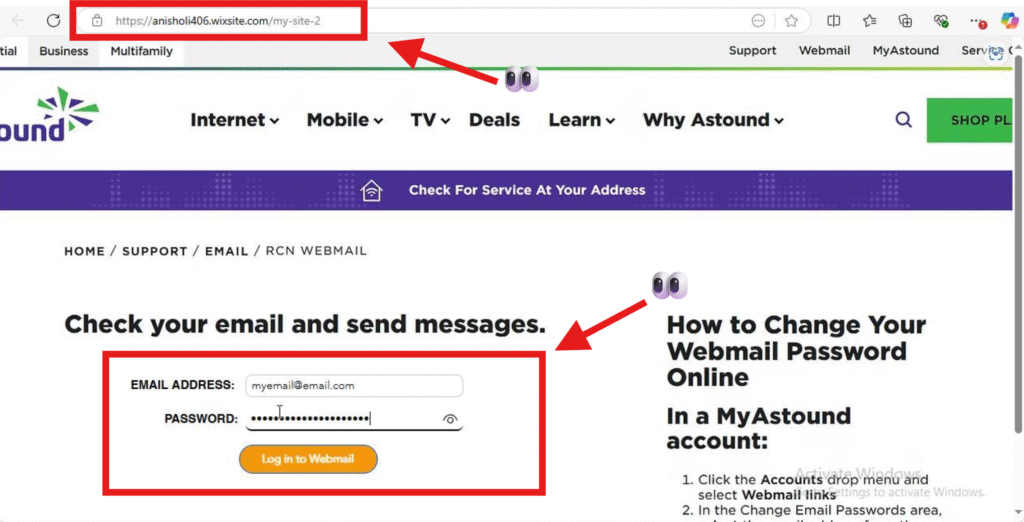
Secondary Stage on Wix
After interaction, victims were redirected to a Wix-hosted site that delivered the malware and gathered credentials.
URL (defanged):
hxxps://anisholi406[.]wixsite[.]com/my-site-2
Why This Matters
The campaign abused well-known hosting platforms, increasing its apparent trustworthiness.
Emails sent via an authenticated third-party account bypassed basic filtering.
Malware used Microsoft Edge command-line abuse for silent execution.
Technical Summary
Execution: via
msedge.exewith non-interactive flags.Payload: dropped files into hidden application folders.
Persistence: registry keys under telemetry paths.
Techniques: process injection (
WriteProcessMemory,CreateRemoteThread).
What You Can Do
Verify sender domains, not just display names.
Be cautious with login pages hosted on free/public platforms.
Enforce MFA on all business accounts.
Report suspicious emails promptly.
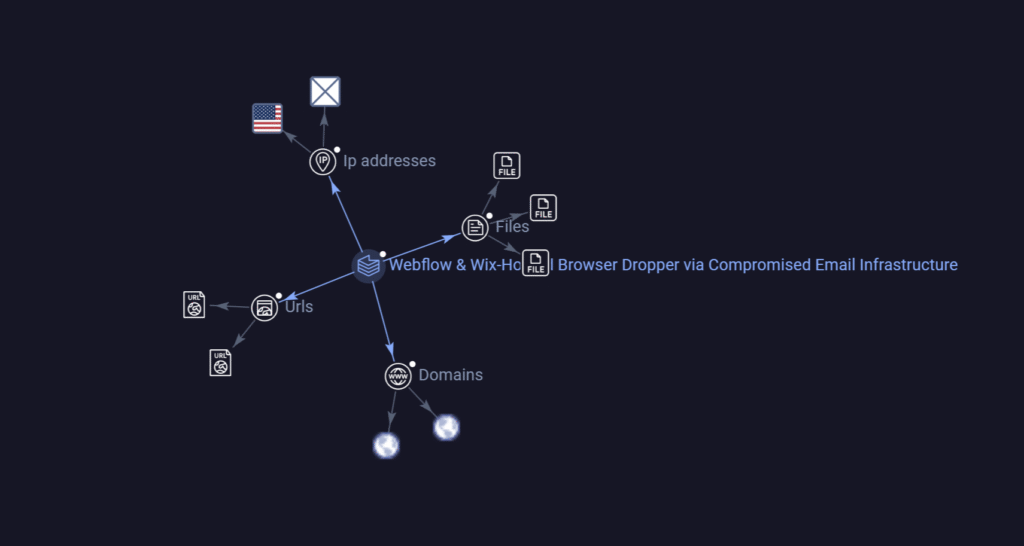
VirusTotal Graph
We have published a related public VirusTotal graph here:
🔗 View Graph
Key IOCs (Defanged)
Malicious URLs
hxxps://myastound[.]webflow[.]iohxxps://anisholi406[.]wixsite[.]com/my-site-2
IP Addresses
104.18.36.248146.20.161.107
File Hashes (SHA256)
5f63beaaefa8bfa3a5564e970ab0b831cdcb0999b6c07f3c748f6674d005bc51e873620645d6cfc6c5403a927609d6337aec31c0577e8c9248758b8cac582538
Email Indicators
From:
[REDACTED EMAIL](appeared as “MyAstound”)Authenticated Sender:
[REDACTED]SMTP Server:
[REDACTED]MIME: HTML with inline content
Detection (YARA)
We developed a YARA rule to detect this dropper, available in our GitHub advisory and VirusTotal collection.
Final Note
SaberGuard normally keeps incident intelligence internal. In this case, due to the abuse of trusted platforms and potential impact to users, we are sharing this report to help the community defend against similar campaigns.
We coordinated with affected vendors, who confirmed and executed takedowns promptly after being notified.
Stay alert. Stay safe.
SaberGuard Threat Intelligence Team